Futaba _ Webs 🕸🕸🎃🕸🕸
What is Ransomware? 🕸🕸🎃🕸🕸
Today I’m going to be going over Crypto malware/ransomware and how to fabricate your own for educational and study purposes.
🎃 Article 🎃 Glossary 🎃 Catalog 🎃 Home 🎃 Search Mode🎃 Article Glossary
🕸 Synopsis 🕸
Today I’m going to be going over Crypto malware/ransomware and how to fabricate your own for educational and study purposes.
🕸 Article Topics 🕸
I'll be discussing the following topics in order: 🎃 What Is Ransomware? 🎃 Importing Serialization Module You can click on any of the topics to simply check that one out if it interests you! NOTE: Articles are read from LEFT to RIGHT via 2 columns! Read the first column all the way down and then move to the next one!
🕸 Key Links 🕸
Here's a quick run down on all the main links that are in the article in case you want to check them out first. 🎃 LinkedIn Version 🎃 Patreon Version 🎃 LIVE Demonstration 🎃 Source Code (DOWNLOAD AT YOUR OWN RISK)
🎃 What is Ransomware?
What is Ransomware? 🕸🕸🎃🕸🕸
What is ransomware? Before I answer that question, I first need to explain to you what FDE(Full Disk Encryption) is. FDE is basically stuff like Bitlocker, where it enumerates the file system and encrypts data on the system in order to prevent data theft. In this case, it’s used for defensive purposes. BUT, what if I told you, it could be used maliciously? That’s what Ransomware is. It's a form of crypto malware that uses FDE to maliciously enumerate and encrypt file system data, holding it hostage, with the crypto keys left in the hands of the attacker, forcing the victim to pay a ransom in order to retrieve the keys to decrypt the data. The real data is excavated off the system in the process with the encrypted version remaining on the system.
Now you might be asking yourself, how do hackers create such complex and intricate malware? It must be so complex and time consuming to write right? Well... it's actually not that hard to write. All you're really doing is combining basic file disk enumeration tactics with either asymmetric or symmetric encryption methods, and some other things to spice it up a bit. I've actually prepared a test sample for today's study, as well as a demonstration video to show you how the code works.
Link to the main the demonstration video can be found here.
Link to the main Code can be found here. IF YOU WANT TO BROWSE IT SAFELY JUST GO TO MY GITHUB PAGE AND VIEW "PYTHON-PENTESTING TOOLS" TO VIEW IT FROM THE BROWSER THAT WAY AS WELL.
Importing Serialization Module 🕸🕸🎃🕸🕸
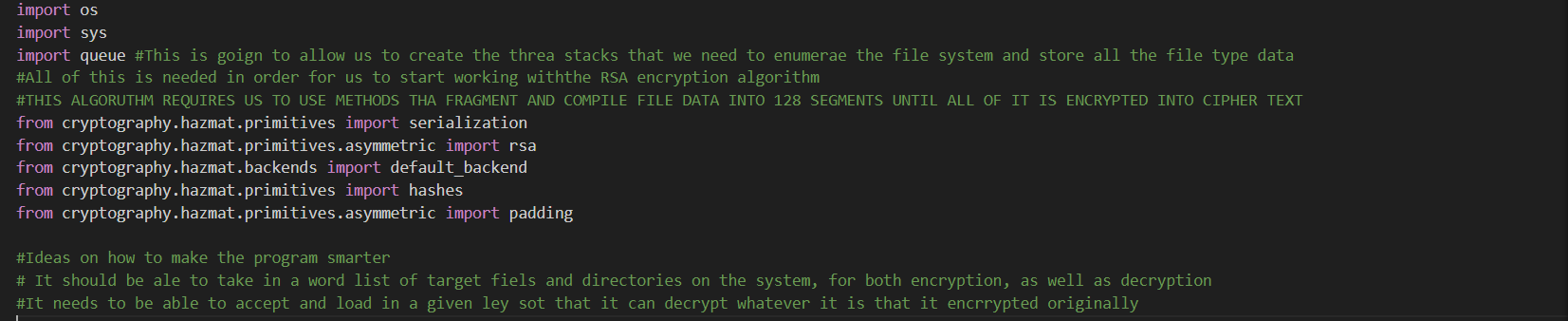
The first thing my code is going to do is import the serialization module and any sub modules with it: RSA, hashes, padding, etc. We need this in order to: create, format, as well as add things like padding and hashing in order to add key stretching, which adds key complexity to the algorithm. What is "Key Stretching"? Key stretching allows us to create longer & more complex crypto keys of a smaller size. This makes the crypto key much harder to deduce via cipher text analysis attacks, as well as allow max computational performance. Typically the larger the key, the longer it takes to encrypt/decrypt. We’re also going to add in the main os/os.sys modules to send shell code commands to the main system, as well as create any directories and pivot the system for enumeration.

If you like to see the more advanced version of this article that talks about methods that can be used to mitigate, as well as any videos included, SUBSCRIBE TO MY PATREON CYBER SECURITY TIER!
If you enjoyed this post give it a thumbs up! I’ll be keeping track of whose reacting from now on as there is a “special” reason for it. Just know the more you support my content the more there is in stored!
- The Hacker Who Laughs 🕸🕸🎃🕸🕸







