
I’ve participated in various high level complex CTF challenges, some of which landed me interviews at companies that had them as a part of their hiring process such as: “Security Innovation”, “Brainnest Consulting”, as well as “Chip Scan”. I also do a bunch of platforms like HackTheBox and TryHackMe, as well as the many 6 that are available on “Canyouhack[.]us” which was provided by “Security Innovation”. I’m also a Pico CTF competitor, and have even done a few high level forensics challenges that involve high level cryptanalysis techniques to decipher hidden data, as well as rebuild, analyze, and compile them. All of the CTF’s I’ve participated in inspired me to create my own known as “Futaba’s Playground” - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

I wrote a test sample to demonstrate how ransomware targets and infects a victim system via file enumeration and disk encryption tactics such as RSA and AES encryption. For this test specifically I am only using RSA encryption. The code basically creates a directory with a series of files with a bit of sample data in them, creates crypto keys to use for the experiment, enumerates and locates all the root files in the folder, and then handles them via encrypting the files, showing you the cipher text, and then reversing the process to decrypt it in front of you. It even tests the keys by asking you to input data when it launches so that you see the program works. - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

I've always wanted to have one of my rubber ducky scripts write its own code In a cool way, so I figured why not combine that with a LAN turtle. I'm even working on a version of this that acts as retro malware to disable security systems in place, allowing me to install any backdoor. - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

I wrote a Man-In-The-Browser exploit that is able to sit in place via the use of exceptions to monitor and track end user browser sessions to keylog facebook credentials from the end user. I ran into a HUGE issue during trial and error with the code. Whenever the end user would clickoff off the page, the code would be unable to find the form elements, breaking the code. What I NEED it to do is, when the end user leaves the page, or should they be on the same site but the code can’t find the elements, is for the for loop to break, bringing us back to the main while loop so that the process to check for sites begins again. To get around this I set up an exception handler. - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

This is a TCP Client that I wrote that connects to a server in a listening state on a victim machine, that can check the OS and version of the system, and then install and run payloads I set based on that, even tools that I might need to pwn the system. I’m upgrading this in the future to combine data encryption to mask my network traffic on internal networks to stay hidden for exploits. - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

This is a TCP Server that I wrote that listens on a victim machine for TCP Client side connections, so that it can interpret and handle any and all shell code commands that are sent by the botmaster. I’m upgrading this in the future to combine data encryption to mask my network traffic on internal networks to stay hidden for exploits. - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

This is a script that I designed that solves one of “Security Innovations” first SQL injection based CTF’s. The script is able to inject a payload into the URL parameter of the web server while pre-loading a cookie session that has been assigned to it, solving the challenge, and storing the results for us in a file, in which we can parse through to check for the flag. - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸
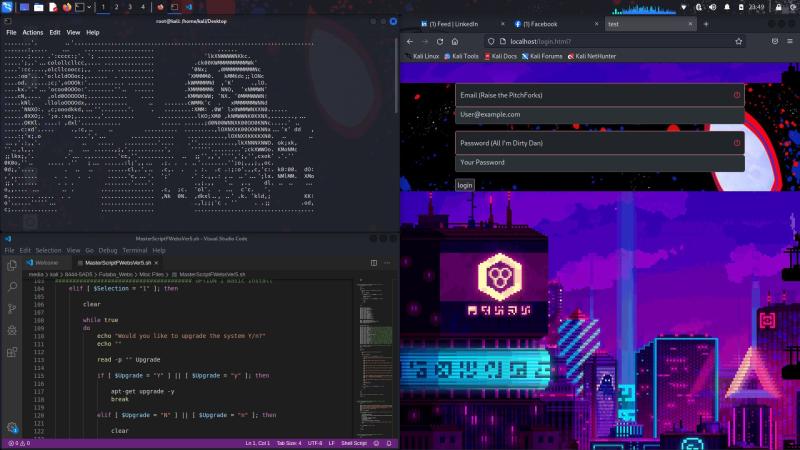
This is a custom portable CTF server that I wrote in: HTML/CSS/JS, and PHP. Further languages used are SQL for the backend of the database which is MYSQL. The server is designed to allow you to pentest wherever you are locally vs the traditional meas of having to be connected to the internet in order to engage in web application pentesting CTF challenges, allowing you to get practice wherever you are on the go. It’s also home lab friendly and allows you to practice network penetration testing as well, and includes a variety of challenges that test a lot of your hacking methodology and skill sets. You’re going to have to apply yourself and LEARN if you want to secure all “11 flags”. You can run this challenge as either locally on your system, or on another system that you can run either directly or vm machine. This makes it more accessiible to all users. If you have nethunter you can also participate in the challenge as well from you phone if you wanted to try mobile hacking. THIS DOES RUN ON NETHUNTER AS WELL THE SAME WAY. YOU NEED TO MAKE SURE YOU ARE ROOT WHEN YOU RUN NETHUNTER SO THE SCRIPT WORKS CORRECTLY OTHERWISE IT WILL CRASH AND FAIL! - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

I’ve included a safe UDP backdoor to run that only works on one system via 2 terminals. I’ve excluded the full version for safety purposes that utilizes TCP/IP in order to allow for remote data communication between said systems on the networks. Feel free to check out the SSH version. I’ve also created my own personal MITB(Man in the browser attack) program, that will launch a total “real” chrome browser (read the code in the description to download the module needed to run the program), which will keep track of any sites written in the code, and will log it down into a text file. For safety purposes it only tells you whether you visited the site or not. I’ve also written my own personal RSA encryption/decryption tool you can use to secure data. The program has a manual mode I’ve written that will explain how to use it. I primarily use python to program a series of low-level networking tools: Client/Servers via TCP, UDP, and SSH, HTML and flask Servers, as well as network sniffers to scan and monitor traffic on networks by sending UDP packet datagrams to wait for responses and see what machines I can talk to, as well as interacting with a variety of different network protocols. I also use python to develop: Encryption/Decryption tools, Man in the browser attack programs, mapping web applications, web brute forcing, as well as to develop trojan programs that I can update and communicate with on different systems, as well as for SQL injection attacks. I’m learning machine learning with python at the moment, and I do also use it to develop fast GUI’s for pentesting tools using PYQT5. - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

This is an interchangeable rubber ducky script I wrote designed to run and execute various payloads. For demonstration purposes I’ve provided a safe version of the code you can run and script onto an arduino board that utilizes a micro USB port (The arduino Keyboard library only works with those types of boards). Simply load up the arduino program and sketch “KeyboardInjectionLINUX.ino” to the board and the sample code will run. I’ve also included a set of functions in a text file, that you can use to edit and swap out functions in the original code should you wish to. Have fun!!! - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

This is a second build of a penetration testing app I've developed that is meant to automate a variety of the different tools I've written. The interface only includes code that has been fully tested thoroughly. Any others, feel free to browse and look at it. You won't see it in the interface but it's there in case you wish to see it. The following to look at first are: Bash_Interface.py (This is the main interface) LinuxInstall.py (Installs all needed components, including PYQ5 in case you don't have it installed. Also compatible with windows via pip installer) Installer Module.sh(Script that will install all needed compilers for Linux should you not have them installed) - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

Inspired by Marcus's drone from Watch Dogs 2 and as a tribute to the series, I'm developing a penetration testing drone, it's sole purpose, to fly around capturing packet data, as well as cracking Wireless encryptions, integrating the use of a raspberry pi zero to host my UDP BackDoor Server program in order to communicate with the drone and see what's on the pi as it's flying. Think of it as a flying wifi-pineapple. When the drone boots up, the pi zero will auto login, where a set of scripts will run, starting up the UDP Server. The flight controller for the drone is built up from scratch, rather than using a pre-built one. The drone will take a series of commands from the transmitter, the controller, also built from scratch (keyboard input option available as well), and depending on the value read from the analog of the joystick module, will move the drone either: forward, backward, left, right, up down, and shifts the values of the signal values sent to the ESC's of the drone in order to move the drone accordingly, all calibrated properly. The drone is still in prototype phase, and is near completion. In the future I will be diving into how to facial recognition software, which I will build from scratch in order to build a true replica of Wrench from Watch Dogs 2, his face mask that acts as a build board, where his facial expressions are scanned by the mask in order to display a a set of emojis that show his emotions. - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸
Today we are going to be talking about how to build a custom backdoor exploit in Python3, as well as what RCE is, including various methods to achieve it. These two techniques are your bread and butter and are what you’ll be going for during a lot of pentests, CTF challenges, etc, regardless of how you go about it: SQL injection, OS command injection, remote file inclusion, etc. It’s really all the same. If you’ve ever noticed, during a lot of big hacks, one of the most common things that ALWAYS happens is that the attackers somehow discover a way to RCE the system, allowing them to gain backdoor access and formulate something called a “botnet”, allowing them to deliver various payloads and command and control the network. Before I dive into this, as always I want to get you up to speed on some terminology so that you understand what’s going on. Let’s go over the main TCP/IP handshake so you understand the overall process. Disclaimer: As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let's begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today we are going to be talking about ARP poisoning and how to poison a network. A lot of this is going to be heavy networking based, so do mind your fundamentals. I'll explain some stuff along the way. As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pentest on anyone's network unless it is your own, or you have permission to do so. - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

Today we are going to be covering the Shodan API and how to use it for CCTV hacking to tap into camera feeds, as well as how to gather information about various IoT gateway devices on the internet and exploit the services on them. This is also going to dive into complex topics like: port forwarding, router exploitation, the routersploit framework, the metasploit framework, as well as how the internet works under the hood. I'm not going to directly tap into a camera feed live as that's illegal (even if it's a public cam for a park), but I am going to show you how to talk to specific ports using an IP address, whether it be in numeral format or alphabetical format. It's the same process you'll be using to tap into camera feeds should you find an open port. For this demonstration, since we'll be using metasploit for it, you're going to need a Shodan premium membership to get a lifetime API key(s). Sadly, Shodan now requires you to be a premium member if you wish to use the API freely. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let's begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I'll be covering SQL injection and advanced fuzzing and filter bypassing techniques you need to know to be a successful pen-tester. You can't avoid not knowing this as you'll see it regardless of what side you are on: blue team, if you are defending against it, or red team, if you are checking if it's a weakness in the system. As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, lets begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, I'm going to show you how to make your own custom LAN turtle Rubber Ducky using Arduino. This is going to simulate connecting the target system back to a server side, much like a meterpreter shell, so that we can pipe over commands on our end and control the target system. The two scripts that are going to be used are the ones from the previous article on "How to Botnet". The client side is going to be integrated with Arduino, where it will will write its own code live and connect back to the server, whereas the server side, the python script, is going to sit in a listening state on the system, waiting for the client to connect to it so it can be fed instructions from the client side to control the system. Traditionally you always want to have the server sitting on the victim system so that you can connect and interact with it, but nowadays making your back-doors peer to peer is actually best because it allows your setup to be more versatile. For safety purposes, it's just going to connect back and that's it, nothing else! The real version that is unsafe to use stays with me. Sadly, this is one of those projects that you NEED to have the right equipment for to pull off, but you can still follow along the 2 demonstration videos here. One, that shows the code being automated, and then another, of me connecting it live in front of you as proof it works. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let's begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸
Today I’m going to be going over Crypto malware/ransomware and how to fabricate your own for educational and study purposes. But before I start, I would like to mention as a disclaimer that I by no means condone any form of illegal behavior you might use this information for. It's STRICTLY for educational purposes ONLY. Due to the nature of how long my posts will be getting in the future I will be writing them in main news articles so I can fully flesh them out better in full detail. Link to the main article for the video and explanation is in the link below. Any and all major past content I’ve made will also be made available via my newsletter article following soon. - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

SOOOOOO, as promised, here is the list of any and all resources I wanted to openly share of mine that I personally recommend and use all the time. It's a special celebration for finally reaching close to 300 connections on here. If you would like to help other people have access to HIGH QUALITY resources so they can learn, then I suggest MEGA sharing this so that connections in your network see it! - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸
Today we are going to talk about Social Engineering, specifically, a "man in the browser" exploit, as well as what social engineering is and how threat actors use it to exploit and leverage a system to gain access. There are various forms of social engineering, and we'll cover them all here today. Social engineering is one of the most commonly used tactics, as well as something that is known as a physical hack. As always, before we dive right into this, some terminology needs to be explained so that you can follow along with the article. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let's begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, in order to celebrate the launching of my new website, I have a special article for today. It's going to feature the first episode of "Mr.Robot", where Elliot hacks a pedophile. We are also going to talk about the TOR Onion protocol, as well as how to bypass it. We are also going to discuss online anonymity, and how to setup and configure TOR so you can be "truly" anonymous. In order to discuss this I need to go over the 3 layers of the internet: The surface web, deep web, and dark web. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let's begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Self-Taught Cyber Security Professional with a background in Software Engineering, IT Technical Support, Security Engineering, and proficiency in Electrical engineering and Reverse Engineering. I have a love and passion for offensive security. I reverse engineer various core API’s and technologies in order to explore and fabricate new ideas that will make my projects come to life. I use my Software Engineering skills to design custom exploits and penetration testing tools, and CTF servers that demonstrate my Security Engineering skills and ingenious ingenuity. My Electrical Engineering skills allow me to devise various custom tools such as keyboard injection exploits that manipulate the virtual keyboard API of a system in order to inject payloads and bypass security measures for security testing, some with the ability to write their own code, which I use to extend further C/C++ Win32API and LinuxAPI exploits along with python scripts. On top of being proficient in C/C++ I’m also proficient in 13 programming languages in total, my main ones being: C/C++, Python3, Bash, SQL, HTML/CSS/JS, PHP, and of course a bit of Powershell scripting as well. My IT skills are on par with level 4 tier experience. I use my reverse engineering skills in order to deduce probable causes and solutions for technical problems. Reverse engineering is my specialty and is how I learn. Given my level of ingenuity, I was allowed to operate above my tier level and demonstrate my skill sets to the fullest and solve lots of complex technical problems at the companies that I worked at, including the infamous Pfizer Pharmaceutical company, which I have thorough documentation of in my research portfolio. My skill sets won’t disappoint you! Check out my work and my research. I take pride in what I do as a professional hacker. - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸

Futaba_Webs is a new brand I’m starting that focuses on developing a series of unique penetration testing tools with style, both software and hardware wise. I also develop and create educational resources that will help people learn how to program, as well as paint the clear pathway to the cyber security field and all it’s intricacies. The most difficult part of learning anything is knowing where to start. - The Hacker Who Laughs 🕸🕸🎃🎃🕸🕸
I’m a self-taught software engineer with a background in cyber security/penetration testing, and have been programming for over 11 years now. One of my specialties is reverse engineering. I like to reverse engineer various core API’s and technologies in order to explore and fabricate new ideas that will make my projects come to life. My favorite video game series known as the MBNS(Megaman Battle Network Series) inspired me to want to learn how to code/program.
Futaba_Webs is a new brand I’m starting that focuses on developing a series of unique penetration testing tools with style, both software and hardware wise. I also develop and create educational resources that will help people learn how to program, as well as paint the clear pathway to the cyber security field and all it’s intricacies. The most difficult part of learning anything is knowing where to start.
The name Futaba_Webs was inspired from my list of favorite video game characters that are hackers: Futaba from Persona 5, Wrench from WatchDogs 2, and Sombra from Overwatch. The other half of my name, Webs, is inspired from my love of the way of the spider, Spider-Man, my favorite spider(s) being, Spider-Gwen and Superior Spider-Man.
This iconic phrase you see all the time on all of my stuff is inspired from DC’s “The Batman Who Laughs”. The pumpkins and the overall theme of where I’m going with them is inspired from “Jack-O'' from my favorite fighting game series of all time “Guilty Gear “, as well as my favorite Marvel SuperHero, “Spider-Man”. The overall theme of this in the long run is to create my own version of a “Spider” that combines all the iconic themes together.
So today, I wanted to talk about WIFI hacking, how to perform it, as well as how to defend against it. Link to the demonstration video is at the end of the post. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let's begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, in celebration for women's history month, I am going to be talking about the vital role that women play in technology. But first, a MAJOR warning/disclaimer to those reading this article. Disclaimer Any and all forms of sexist behavior and inappropriate comments are STRICTLY forbidden for this post. This is a month where we celebrate the rich history of women and the major overall role of women in tech, in my case the big contributions for tech that they have made over the years that they haven’t received the credit that has been long overdue. Without women in tech Cyber Security and all forms of modern technology, as well as programming languages and methodologies wouldn’t exist without them. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I am going to be handling one of the most TRIGGERING topics in Cyber Security. PROGRAMMING! Anti-Programmers Beware!!!! People often feel there should be a motion for programming to become less relevant in Cyber Security because they never code on the job, and that it increases the barrier for entry way into Cyber Security, but they couldn't be more farther from the truth. I’m going to explain today why programming plays an important role in Cyber Security and why it’s important to learn how to code. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let's begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, we are going to go over one of my favorite exploits, the EVIL TWIN ATTACK! This exploit focuses on kicking end users off their main network or posing as a legitimate one for end users to connect to so we can phish them and compromise sensitive data. Typically this is done using something that is known as “Wifi Pineapple” from Hack5. The tool is designed to masquerade as a legitimate network access point and trick end users into connecting, posing as the router and intercepting any and all exit node traffic data that is sent to it, stripping it in the process to bypass secure communication methods. It interconnects with the main access point in the process and forwards the communication on its behalf to your target destination as if nothing ever happened. But, WE'RE much better than that. You shouldn't have to rely on someone else’s tool to get the job done. Are you a hacker or aren't you? I'm going to show you HOW to perform the exploit without one and the raw natural science behind it. HOWEVER, since this involves WIFI hacking and network penetration testing, I recommend you check out my previous article that covers more on this topic as it goes over a lot of terminology that you might be unfamiliar with. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let's begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today we are going to be talking about the many malware types that exist. As many of you know, I LOVE writing malware and various penetration testing tools, as well as reverse engineering them in order to see what techniques I can pluck off from them. Sadly, because there are so many, I can’t talk about all of them otherwise the article would be 7 pages long, so instead, I’ll talk about a select few. If you would like to get more into malware development and learn a couple of projects, check out some samples on my GitHub page. Any and all code is well commented and documented, so you should have no trouble understanding what each line does. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, we are going to go over something fun, and do a CTF, one which involves cipher analysis and a bit of binary analysis in order to solve it. This is also going to cover a bit of obfuscation techniques such as using an encoder to mask the contents of the file to change it’s overall file structure and throw off either as A giant chunk of the demonstration for today is going to mostly be video, but the article is going to explain what I’m doing in the video as you watch me solve the challenge LIVE. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, we are going to cover mobile hacking, as well as how to hack into various OS systems types: Windows, Linux, Mac OS, Android, etc, as well as how to pull off some cool stuff with the meterpreter shell: tapping into camera feeds, enumerating contact information, and even how to enumerate text messages from mobile devices. We are also going to cover how to create payloads and format and encode them with a tool from the metaploit framework called “msfvenom”. For today's demonstration, I’m going to demonstrate how to hack into a Linux system using a meterpreter payload. Everything I am going to show here, carries over to the other platforms I mentioned since it’s rinse and repeat. I’ll include any and all special commands that are tailored for mobile hacking while going over the exploit. For this tutorial I highly recommend you check out my article on how to botnet, which covers a lot of the core basics on how to use the metasploit framework. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, I wanna go over an important topic about how NOT to get into Cyber Security. Today is the opposite day, so do the OPPOSITE of what I say! This article idea was inspired from none other than Ricki Burke, founder at CyberSec People One of the most common and most illogical misconceptions about trying to break into Cybersecurity I’ve seen is the notion that you don’t have to be technical in order to pursue this field, on top of many other things that I’m going to discuss in this article today. I want you to be mindful, NONE OF THIS IS GATEKEEPING. You need to hear the TRUTH in order to pursue Cyber Security. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I want to talk about a hot topic that has been on the rise in regards to Cyber Security news lately, even prior to its official announcement… THE BANNING OF THE FLIPPER ZERO! It’s no speculation that a lot of the news surrounding it lately was going to lead to its inevitable ban in the U.S. The tool is so popular in regards to what it’s being used for, that it could potentially be banned on a global scale, as it’s also in the process of being banned in places like Canada that also see it as a threat. For those that don’t know, the Flipper Zero Tamagotchi is being used for motor vehicle car theft. The tool is so seamless and easy to use that even people that don’t understand anything about hacking could pull it off, hence its ban being set into motion. But… What if I told you it’s pointless to ban it? I want to talk about why it’s pointless to ban the Flipper Zero, as well as some basic things that could be done to prevent motor vehicle car theft with it, as well as other methods similar to it. I also want to talk about how Cyber Security is a game of chess, and how it is meant to be played to deter Cyber threats. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I’m going to talk about a topic that often comes up quite a lot for those looking to break into Cyber Security, which is how to find a mentor. A lot of people, despite all the free learning and resources available, often seek a mentor, someone who guides them throughout their journey. I’m going to talk a bit about the importance of a mentor and how they play a pivotal role in your career, as well as the MAJOR benefits of having one. I’m also going to dive into a sensitive topic as to why it’s hard to find a mentor, as well as the general etiquette and relationship dynamic between mentor and mentee. This is to help show you the do’s and don’ts when looking for one, as well as how to maintain one should you happen to find one. Mentors, GOOD ones, are HARD to find, so if you happen to land one, MAINTAIN IT! I’m also going to address the BIG dangers of free learning and why it doesn't work for everyone. This will better establish the main reason why people still seek mentorship even though they can learn for FREE at NO COST on their own. This article is made specially after the announcement of a hybrid mentorship program that I’m working on that will be available soon! You can check out the details on my linktree here if you would like! MORE COMING SOON FOR IT! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, I’m going to go over a fun topic, one that is surprisingly not well talked about enough that quite frankly should be. I’m going to go over the various types of hackers, or “hats” to be more specific. There are seven types: white, black, gray, green, blue, red, and purple. Each hat has an agenda and purpose and plays a HUGE role in protecting our digital landscape. I'm also going to go over what a script kiddie is since there is A HUGE difference between them and one particular hat that is apart of the main category that is going to be discussed today. You’ll also get more in depth as to why my head line says I am a “Gray Hat Hacker”. A lot of people, and I’ve talked with a few, have no idea what the hat’s actually stand for and why we use them. It’s important, especially if you are going to be a part of hacker culture. It will come up in topics, so it’s best you know what they all stand for. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, I want to talk about the dangers of mobile end devices, how everything is connected, the risks they pose, as well as how they can be critically exploited by threat actors. This article topic was inspired from a recent thread I was in where a woman’s mobile device got hacked and it led to various parts of her life being compromised in the process, putting her overall safety as well as that of her friends and family at risk! I wanted to raise more awareness and teach people how to protect their digital identity! A lot of the article will be me addressing what happened, as well as remedies I gave her to protect herself. This is also the start of a new series that is called the “DANGER!” series, where I raise more Cyber Security awareness about critical flaws and vulnerabilities within system infrastructures, including any protocols and data communication methods, where I also talk about mitigation strategies that can be used to prevent such threats. There will also be a LIVE demonstration for those of you who are subscribed to my patreon, to see how closely I can exploit mobile end devices in order to retrieve any and all sensitive data from the mobile end device! There will also be a step by step exploit guide walking you through the entire process as well, and how to gelocate someone’s phone and turn it into a GPS tracker! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I’m going to cover the ins and outs of some of the core basics on how to use the burp suite proxy server for ethical hacking. The key point of this article is to discuss the main features that are commonly used, as well as walk through on how to use them. There will be live video demonstrations of course, but like always, that is for the PAID patreon members. I’m also going to show you how to botnet and command and control with the burp suite proxy server and how to strip any and all network traffic on a multitude of systems using it! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today's EXCLUSIVE article, as well as for the rest of the next 2 EXCLUSIVE issues, we will be covering full in depth on the very material that I’ve provided you with in my free samples: footprinting and information gathering, scanning and enumeration, as well as attacking various systems. For today we are going to focus on Footprinting and information gathering regarding web application systems. This will get you into the feel on how to conduct the first phase of a penetration test against a web application server This will include a LIVE 14 min video demonstration that is ONLY for patreon members a part of the Cyber Security Tier on my patreon!. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I want to talk about SSO and OpenAuth, two forms of authentication methods that are highly common and popular in today's security infrastructures, and discuss the major critical flaws they contain from a fundamental standpoint. For the sake of the argument, I will be focusing on the initial main premise of the two, and NOT advanced versions of them which have received some security upgrades for obvious reasons. I want to focus more on talking about the overall design of the two methods and the BIG flaws in them. This article is a part of the new Danger! Series I’m launching, which is where I raise more Cyber Security awareness about critical flaws and vulnerabilities that exist within various system infrastructures, including any protocols and data communication methods, and the Dangers of what could happen should they be exploited to the fullest extent. I also go over various mitigation strategies that can be used to prevent them as well. If by chance there is an exploit video for me showing the full potential risk, it will be included in the advance version of this article for PAID patreon members only! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I want to talk about DLL/Code injection, which are forms of hooking techniques that allow an attacker to manipulate the overall function calls within a program to deliver malicious code and or shell code payloads in a covert manner to a system. I also want to explain the key difference between DLL and Code injection, as it’s commonly assumed to be one in the same. They are similar, BUT, are vastly different. This allows us to control all the key function calls that control the windows system software wise, while also allowing us to manipulate and control key function calls that communicate directly with the hardware on the system, allowing us to control it. This allows an attacker to bypass various forms of security, such as application firewalls for example, allowing them to exploit the system further and gain higher levels of privileges on the target system and exploit it further, extending their reach and possibly infecting more systems and the overall network infrastructure together as a whole. I will be going over any and all function calls that are used to pull off the DLL/Code injection exploit, as well as the methodology and science behind it. Which will be available for PAID patreons only. There will also be a follow up video in the next bi-weekly issues that will feature a live programming video to demonstrate the process. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today we are going to be covering how to extract metadata from images, which can be used in order to find someone’s location with just a mere photo. We are also going to go over various methods that can be used in order to wipe the metadata from any and all photos that you take. When you upload a photo to stuff like Instagram for example, websites tend to have a process where they handle and wipe any and all metadata from the main photo image to preserve end user privacy. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Hellloooo Everyboddyyy! This is something that has been long overdue (for a month haha). WE FINALLY REACHED 500 CONNECTIONS!!!!! Couldn’t have done this without all the support form you guys: reacting to all my stuff, sharing, commencing, engaging, some of you even becoming full on patreon paid followers! I wanted to write a special article and give out some more resources, as well as any guidance or advice I can give you that will aid you on your Cyber Security journey, specifically for offensive security and penetration testing. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I want to talk about Network Security, specifically misconceptions from a few networking security methodologies that we commonly assume are fully secure in terms of defending our network infrastructures. The goal is to highlight the flaws within them, and prove a major point, one that is commonly seen in today’s Cyber Security practice, which is the over reliance on tools and or security methods. I will be talking about stuff like: MAC address filtering, port security, and even stuff like hiding SSID’s, and the various ways they could easily be bypassed, and methods that can be added or stacked to improve upon them. This article is a part of the new Danger! Series I’m launching, which is where I raise more Cyber Security awareness about critical flaws and vulnerabilities that exist within various system infrastructures, including any protocols and data communication methods, and the Dangers of what could happen should they be exploited to the fullest extent. I also go over various mitigation strategies that can be used to prevent them as well. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today we are going to be going over what cookie session hijacking is, and how to perform it. I want to talk about cookie session hijacking, the overall risk it poses for our digital landscape, as well as how to defend against it! This is also a common means to breach a system you WILL see in a lot of CTF challenges, so PAY CLOSE ATTENTION IN THE VIDEO to how it’s done. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today we are going to be covering our first tool that can be used for ethical hacking…. Zip2John. Ever ran into a situation where you needed to bypass a secure zip folder for a CTF challenge, or just overall in general? Fear NOT! This tool will help you! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today’s demonstration will be a little lab exercise that you can set up to practice using my backdoor script that can be found on my github page. THIS LAB WILL REQUIRE YOU TO WATCH AND FOLLOW TWO VIDEOS AND GUIDES STEP BY STEP TO PULL IT OFF! YOU WILL NEED A SEPARATE SYSTEM TO FULLY SIMULATE THE TEST (OR VM IF YOU PREFER) The VM setup is going to be done on kali nethunter BUT, the instructions for this carry over to ANY system that you want to test against the backdoor server on I recommend checking out my video guide on how to setup kali nethunter in case you want to do the lab this way! It’s FUN and you get to apply Mobile hacking like a PRO. The goal of the exercise is to show you how to: setup the backdoor exploit, experimenting with kali nethunter (if you happen to have it setup), show you how to set up an apache2 server to deliver payloads, crack passwords with John the ripper so that you can pop the SSH service on the main system, and then show you how to exploit the system further. WE ARE GOING TO RUN A SIMPLE PING SWEEP VIA THE MAIN COMPROMISED SYSTEM TO PULL IT OFF, GOING UNDETECTED!! Due to the nature of how I want you to experience a “limited” shell which you’ll often run into, you’ll notice I’ve made it a bit “less interactive” to a degree so that you HAVE to get into the habit of finding ways to upgrade the quality of your reverse shell to a system! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today’s lab will be the more hands on part of how to setup your first arduino project HANDS on. Like I’ve mentioned before, this is basically the “hello world” for arduino. Things will get A LOT more interesting once you cover the core basics so you can start building your own hacking tools with it! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

For today’s video, I will be going over how to write the backdoor script from my “Backdoor” article live. Step by step instructions should you need to read them over can be found below in the post, as well as in the main video! This is going to be a 3 part process, where each step I want you to play around with the core basics of what I’m showing you so you understand what I’m doing and how everything works. The first part is this one, how to build the client side of the backdoor connection. The next step will be building the server side of the backdoor, which the main client will connect back to. Last, we’ll get creative and I’ll show you some more complex and how to get creative with it. THIS REQUIRES YOU TO ALREADY KNOW THE CORE BASICS OF PYTHON. The main reason why this is going to be a 3 step process is because you will be learning stuff about software engineering as well, and I don’t want to overwhelm you with too much information at a time! That, and I want you to play around with all the stuff that is covered in the main video each time and ask me questions so that you MASTER it by the time the next video launches. Don’t focus on memorizing the code step by step, that will get you nowhere. Focus on UNDERSTANDING the theory and the science behind that I’m doing. IF YOU DO NOT UNDERSTAND SOMETHING SHOOT ME A MESSAGE IN THE “light mentorship channel” and I’ll answer any questions that are related to the post, as well as any and all content I’ve made thus far! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸
For today’s video, I will be going over how to write the backdoor script from my “Backdoor” article live. Step by step instructions should you need to read them over can be found below in the post, as well as in the main video! This is going to be a 3 part process, where each step I want you to play around with the core basics of what I’m showing you so you understand what I’m doing and how everything works. The first part is this one, how to build the client side of the backdoor connection. The next step will be building the server side of the backdoor, which the main client will connect back to. Last, we’ll get creative and I’ll show you some more complex and how to get creative with it. THIS REQUIRES YOU TO ALREADY KNOW THE CORE BASICS OF PYTHON. The main reason why this is going to be a 3 step process is because you will be learning stuff about software engineering as well, and I don’t want to overwhelm you with too much information at a time! That, and I want you to play around with all the stuff that is covered in the main video each time and ask me questions so that you MASTER it by the time the next video launches. Don’t focus on memorizing the code step by step, that will get you nowhere. Focus on UNDERSTANDING the theory and the science behind that I’m doing. IF YOU DO NOT UNDERSTAND SOMETHING SHOOT ME A MESSAGE IN THE “light mentorship channel” and I’ll answer any questions that are related to the post, as well as any and all content I’ve made thus far! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

For today’s video, I will be going over how to write the beginner source code that you need to create your very own LED light bulb in conjunction with a switch module using Arduino. This is basically the “hello world” for Arduino. Step by step instructions should you need to read them over can be found below in the main video! This is going to be a 3 part process, where each step I want you to play around with the core basics of what I’m showing you so you understand what I’m doing and how everything works. The first part is this one, writing the main code and learning how to read the basic diagram chart for the Arduino UNO board. This is to get you into the habit of learning how to program any module first which is the first and hardest step. Step 2 will be us putting it all together so that you get a live visual on how to set it up. Step 3 will be me showing you around the Arduino IDE, so that you know how to configure boards and various libraries for it. Much like the python one, this first project of ours will be on easy mode, and progressively get harder as time goes on. THERE IS AN END GAME TO THIS! THIS REQUIRES YOU TO HAVE AN ARDUINO UNO BOARD. The main reason why this is going to be a 3 step process is because you will be learning stuff about software engineering as well, and I don’t want to overwhelm you with too much information at a time! That, and I want you to play around with all the stuff that is covered in the main video each time and ask me questions so that you MASTER it by the time the next video launches. Don’t focus on memorizing the code step by step, that will get you nowhere. Focus on UNDERSTANDING the theory and the science behind that I’m doing. IF YOU DO NOT UNDERSTAND SOMETHING SHOOT ME A MESSAGE IN THE “light mentorship channel” and I’ll answer any questions that are related to the post, as well as any and all content I’ve made thus far! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

For today’s video, I will be going over how to install and setup the Arduino IDE for a Linux setup! Majority of all of this will be IN LINUX, to get you used to installing and setting up stuff for it so be warned!! This is going to be a 3 part process, where each step I want you to play around with the core basics of what I’m showing you so you understand what I’m doing and how everything works. The first part is this one, writing the main code and learning how to read the basic diagram chart for the Arduino UNO board. This is to get you into the habit of learning how to program any module first which is the first and hardest step. Step 2 will be us putting it all together so that you get a live visual on how to set it up. Step 3 will be me showing you around the Arduino IDE, so that you know how to configure boards and various libraries for it. Much like the python one, this first project of ours will be on easy mode, and progressively get harder as time goes on. THERE IS AN END GAME TO THIS! THIS REQUIRES YOU TO HAVE AN ARDUINO UNO BOARD. The main reason why this is going to be a 3 step process is because you will be learning stuff about software engineering as well, and I don’t want to overwhelm you with too much information at a time! That, and I want you to play around with all the stuff that is covered in the main video each time and ask me questions so that you MASTER it by the time the next video launches. Don’t focus on memorizing the code step by step, that will get you nowhere. Focus on UNDERSTANDING the theory and the science behind that I’m doing. IF YOU DO NOT UNDERSTAND SOMETHING SHOOT ME A MESSAGE IN THE “light mentorship channel” and I’ll answer any questions that are related to the post, as well as any and all content I’ve made thus far! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, I'm going to talk more about ransomware attacks and how to prevent them. This is to raise more awareness on proper Cyber Security data Hygiene methods, as well as other techniques that can be used to prevent any real damage should this attack connect. This article is also going to feature some of my formal QA answers from a recent interview I did most recently. I recently participated in a formal QA interview for a research group at the University of Washington that focused on Business Impact Analysis, and the best mitigation strategies and tactics that should be applied to better secure our digital landscape. The goal of the research project is to help educate small businesses run by women and other minority groups on proper Cyber Security practices. The QA was led by a woman named Grace Sommers. If you would like all the full in depth answers regarding the QA, you can find it on my patreon attached to the advanced version of this article. It's 9 pages and you can learn a lot about how to properly defend your digital systems from various attack vectors, including various endpoint security methods if that fancies you. This article is a part of the Danger! Series, which is where I raise more Cyber Security awareness about critical flaws and vulnerabilities that exist within various system infrastructures, including any protocols and data communication methods, and the Dangers of what could happen should they be exploited to the fullest extent. I also go over various mitigation strategies that can be used to prevent them as well. If by chance there is an exploit video for me showing the full potential risk, it will be included in the advance version of this article for PAID patreon members only! Ransomware attacks are on the rise, and are a favorable attack method commonly used by a lot of crypto gangs. It's important to know how to protect yourself from these types of attacks. Ransomware, as shocking as this might sound, is EASY to stop, rather, easy to render useless. It's simply a matter of understanding the critical flaw within the attack method itself and what it relies on to execute. I'll also be covering some basic stuff like FDE, cryptography, etc, so that you FULLY understand how the attack method works. Pay close attention to the cryptography stuff since you NEED to understand how it works, both from the perspective of a threat actor, as well as from an overall security standpoint perspective. If you would like a demonstration of the technique, I wrote an article demonstrating how to write the code and perform the technique, as well as a live demonstration that can be found on my YouTube channel. If you would like to see the sample code for it, you can find it in my "Python-Pen-Testing-Tools" in my main Github Repository Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I want to talk about two different types of file inclusion techniques that can be used to exploit web applications: Remote File Inclusion and local file inclusion. I also want to talk about the difference between the two since they tend to be mistaken for one another, as well as a few techniques that can be used to mitigate against them. Today's article will include a video demonstration of how to perform local file inclusion, also known as directory traversal, against a remote web application server. I'll even cover one of the best FREE beginner tools that you can use to apply the technique in a more automated fashion. If you would like to see how to perform remote file inclusion, as well as the best means to do so, then I suggest checking out this video from patreon lab for the TCPBackdoor exploit Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today’s video demonstration I’ll be showing you how to make your own custom HTTP server. If you’ve been watching most of my videos, even some of my meterpreter stuff so far, you’ll notice that when I’m delivering payloads on a local network I LOVE to host an apache2 server that will serve payloads to victim systems on the network. It bypasses any blacklists from the main ISP and default gateway since this is an internal HTTP server and it’s not morally set to block those. BUT, what if you don’t have the means to setup an apache2 server? This is where you get crafty and make one yourself. It comes in handy for a lot of practical applications that allow you to mix it up with past techniques I’ve shown you, and apply stuff that even apache2 and nginx servers aren’t designed to do. Be mindful, I'm not saying you should drop the apache2 setup. It’s a staple and go to tool overall in general whether it be for penetration testing, or simply just web application development to test your site for responsiveness and effects. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today’s Arduino lesson I’m going to show you how to program a potentiometer. The goal of this project is to get you prepared on how to handle analog input for any module in arduino so you can work with stuff like: dials, radio modules, and even joystick input. PAY CLOSE ATTENTION to this project as what you’ll learn here, on top of the other stuff will carry over to what is to come soon and a lot more. These projects will start off easy, but like I said, WILL, get progressively harder and more interesting. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today’s live tool demonstration is going to feature cracking SSH services using two of my favorite CLI hacking tools: Hydra and Patator. Hydra is a commonly used tool that is use to brute force against web application servers, as well as commonly used to crack SSH, FTP, and RDP protocol services Patator is a more advanced tool that is able to work with more services than Hydra, so it comes in handy when you need to crack something that is out of the typical scope of Hydra. It also has much more fine tune options that let you control the overall quality of the attack itself. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, we are going to address a popular topic going around in the latest Cyber Security news outlet, the new Windows Recall feature that’s just released for Windows 11. It’s no shocker that there are some ahem… “major” security related concerns that have been circulating about it for the past few weeks since its official announcement and release. I’m going to talk a bit about how it works, and of course, like always, I’ll explain the dangers of it. In the more advanced version of the articles, I’m going to go over how some of the core API functions work, and how we can exploit them. Much like how in the DLL injection article where I mention there will be a followup article later on with live footage to show the exploit, the same will be the case with this article as well. This is to ensure you have the proper knowledge and that it marinates before we dive into the real thing. Security is something that is HIGHLY neglected during many software development projects. I’ve talked a bit about this before, but if security is not kept in mind, it can lead to some pretty crazy stuff, like for example, OpenAuth and SSO. If you would like to see what I’m talking about in regards to that, you can check that this article. This article is a part of the Danger! Series, which is where I raise more Cyber Security awareness about critical flaws and vulnerabilities that exist within various system infrastructures, including any protocols and data communication methods, and the Dangers of what could happen should they be exploited to the fullest extent. I also go over various mitigation strategies that can be used to prevent them as well. If by chance there is an exploit video for me showing the full potential risk, it will be included in the advance version of this article for PAID patreon members only! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, I’m going to cover an IMPORTANT topic, HTTP request methods. I’m going to keep it real simple and go over all the basics for all of them in full detail so you understand how each one functions, as it’s important in order for you to properly understand how HTTP/HTTPS data communications function on a lower level. We’ve talked about how the internet works, and things like port forwarding, the TCP/IP handshake, etc, but we’ve yet to discuss the actual HTTP methods you constantly see in stuff like burp suite for example. For this article, there will be a video, demonstrating how to use HTTP methods via burp suite. As always, this will be for paid patreon members only. For this article, we are ONLY going to talk about some of the basic ones you should know first: GET, POST, PUT, DELETE. Any other ones mentioned later on will be for paid patreon members only. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

This week we will be going over how to write a more advanced version of the Man-In-The-Browser exploit. It features some new techniques that could be of use to you. I’ll also be covering a few modules in python to stack with the exploit so you can further extend and do a lot more with it. This demonstration will cover how to keylog end user credentials with the exploit, and then post them to a remote server, specifically the one that we wrote in last bi-weekly’s issue regarding how to write a “HTTP Server” in Pyhton3. Pay close attention to this video as we are combining past things we’ve learned to make the exploit 10 times better. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

This week’s tool tutorial I’ll be covering how to use SQLMap to perform RCE execution on a remote system featuring HackTheBox’s “Vaccine” machine”. SQLMap can be used for a lot more than just performing SQL injections and dumping databases that are vulnerable to the technique. It can also be used to perform RCE execution and pop you a reverse shell. I’ll also be demonstrating something that has been highly requested, which is creative more advanced interactive shell upgrades once you land RCE against a system. One of the biggest things you’ll often notice after you land RCE, is that you require a “ptty” shell which is a more interactive legit /bin.bash shell that can execute more advanced, if not all commands on the remote target system. IT’S CRUCIAL YOU KNOW HOW TO DO THIS AS IT’S PRACTICAL AND YOU’LL OFTEN HAVE TO DO SO. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

This week I’ll be teaching you how to program a Joystick module for Arduino. This is part in the making for a more advanced lab that is coming up, which WILL require you to know how to do this. I’ll also be covering some smart techniques and tricks on how to program the module correctly since it can be tricky for beginners to program it correctly on their first try. We’ll be putting what we’ve learned so far about how to program: switches, LED pins, as well as analog all into one go, as well as the overall basics on how to physically setup. There of course will be photos on how to setup the module properly so you can see everything I’m doing. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, I’m going to dive into a super sensitive topic, one that I don't recommend if it’s not your cup of tea. I’m going to be talking about CSAM, which is short for “Child Sexual Abuse Material”. I’m going to talk about what it is, as well as recent activities by various social media platforms that encourage the spawn of it, and how our very own Cyber Security practices can be used to help aid Cyber criminals and other illegal activity on the internet. The main goal for today is to talk about how data encryption and secure communications aid CSAM on various social media and communications platforms: Facebook(Meta), WhatsApp, Telegram, etc etc. Data encryption and secure communication methods such as SSL and TLS, although it can be used to protect end users and prevent interceptions via man in the middle attacks, as well as render data infeasible, it can also aid threat actors and CSAM criminals, enabling them to go undetected and remain anonymous(depending on how smart they are on the internet). I’m also going to talk a bit about how our privacy laws and policies can also aid threat actors as well. We often forget that laws not only protect the innocent, but also criminals at the same time. It’s one of the biggest reasons in the event of a real situation where there is a threat to the safety of others concerning certain forms of data, business infrastructures refuse to disclose it unless there is a certain process they undergo to safely do so. This article is a part of the Danger! Series, which is where I raise more Cyber Security awareness about critical flaws and vulnerabilities that exist within various system infrastructures, including any protocols and data communication methods, and the Dangers of what could happen should they be exploited to the fullest extent. I also go over various mitigation strategies that can be used to prevent them as well. If by chance there is an exploit video for me showing the full potential risk, it will be included in the advanced version of this article for PAID patreon members only! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I’m going to talk about the metasploit framework, what it is, and why it’s a STAPLE tool in EVERY hacker's arsenal, whether it be for beginners or experienced hackers. I’ve gone over how to use it for certain exploits, but I’ve never fully shown: how to set it up, what all the options mean, advanced options, how to chain and combine stuff, etc. I’m going to show you the most practical way to use the framework so that you can effortlessly hack it like a pro in no time. I’m also going to show you one CRITICAL thing that commonly gets overlooked when using the framework. It’s an abundance of FREE knowledge, one that if you know how to use it, you’ll become one of the most skilled and dangerous hackers of all time. Think of the Metasploit as all your “past lives”. You have access to all of that information. You just need to learn how to use it properly. This article will of course be video oriented, and will only be available to PAID patreon members only. It’s no shocker that it’s a staple tool in every hacker’s tool belt, but shockingly enough, due to how times have changed, I don’t quite see it picked up by newcomers or talked about enough anymore. I know it still sees light and people use it, but nowadays I rarely hear anyone post or even talk about it, and it’s one of the standard tools much like aircrack-ng. People forget that a lot of newer tools are based on the original ones that are known and loved by the hacker community. Recently one of my favorite authors (Tags her name), ran into an issue where someone thought recommending Aircrack-NG was a horrible idea due to how old it is, when it is in face one of THE best pentesting tools hands down to seamlessly crack various wireless encryption: WEP, WPA, WPA2, etc. Even most pentesting methodologies or tools mimic it in some shape or format just like with metasploit. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

For today's tool demonstration, we are going to be diving more into the metasploit framework, as well as previous techniques involving IOT hacking to dive into web cam hacking. One of the many features of the meterpreter shell from the metasploit framework, is that it allows you to tap into the camera feed of the IOT device you breached, meaning you can grab live video time footage of the end user, as well as any meta data that will give away their coordinates and location if you would like to strip that using tools we've covered like exiftool. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

For today's software engineering content, we are going to dive into how to write out form requests to implement various HTTP methods from scratch, as well as how to setups basic HTML file from scratch. I will be showing you how to setup form requests, as well as: text inputs, password inputs, submit modules, and lastly, file uploads for an html page. The goal of this, is to get you into the habit of knowing how HTML code works and how to tamper with it. Pay close attention to how I'm writing the code, as you'll need to know this for the upcoming lab that is set to launch soon. Source code, like always, will be in the attachments section bellow. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, I’m going to cover how to program an RF module with arduino in order to send radio waves from one radio module to another. This is going to come majorly into play for the next lab that I have set, as well as one of the biggest projects in the long run, so do pay close attention to how I am writing the code for it. Don’t forget that how to set up any and all modules takes place during the major lab that will be combining all the parts together. The goal for all of this is to get you used to how to write the code, and then we dive into how to physically set all of it up which is the fun hands on part that you all know and love. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, I’m going to talk about WAP security and why it’s important for you to implement it for both home networks, ESPECIALLY HOME NETWORKS, as well as corporate infrastructures. We often overlook this, which can lead to a MASSIVE SPOF that can lead to a massive scaled botnet if we’re not careful with implementing proper WAP endpoint security measures. I specialize in networking overall so I have a lot of fun messing around with penetration testing regarding them. I’m also going to talk a bit about the various creative ways threat actors can exploit an access point to do some serious damage and a lot more. Of course *whistles* I’m just theorizing. It’s not like I’ve been paid to do this stuff before right haha…. *cricket noises*.. AHEM… back to the point of the matter! I’m also going to talk about what SPOF is since it’s a CRITICAL topic that you’ll often come across in Cyber and Information security, WHICH YOU NEED TO KNOW. It’s so important that simply not knowing it is one of the MAIN reasons why we have so many security breaches and bad Cyber Security practices. Lastly, since this is of course the danger series, I am going to address MANY remedies that can be done in order to enhance your overall network security, most of which you probably have never thought of in the first place. I’ve played around with a lot of this stuff, so do take my word for it. This article is a part of the Danger! Series, which is where I raise more Cyber Security awareness about critical flaws and vulnerabilities that exist within various system infrastructures, including any protocols and data communication methods, and the Dangers of what could happen should they be exploited to the fullest extent. I also go over various mitigation strategies that can be used to prevent them as well. If by chance there is an exploit video for me showing the full potential risk, it will be included in the advance version of this article for PAID patreon members only! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let's begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I’m going to address a hot topic, one that has been going around lately since it’s innate birth… WILL A.I. REPLACE US? I’m going to basically debunk some of the most popular reasons why, and why it’s just another tool that will aid us in our daily lives. I’m also going to talk a bit about what A.I.is and how it compares to actual human intelligence since the overall goal of it is to replicate the human mind. I’m also, lastly, going to discuss the BIGGEST downfall that has been leading to a lot of FAILED expectations to be met from A.I, and how the overall introduction of it has affected the overall job market. Recently with the development of OpenAI, which lead to stuff like ChatGPT, we’ve entered a more advanced era of A.I., where it can do a bit more than just “Hey Siri”, or “Hey Alexa”, and query and search stuff for us and return the results. “A.I”has progressed to the point where it’s able to do ACTUAL stuff like: generate images for us, write our resume and cover letters, generate basic code templates, generate animations, etc. I think you get the picture! BUT, don’t be misled by what you see on paper. Not everything translates well. I’m also going to talk about why I don’t like A.I., which is mostly due to the FALSE image that it has implanted in our minds and WHY I’m enjoying it’s slow and inevitable downfall. I’m a HUGE tech enthusiast, and am VERY open minded to many implementations of it. Tech has advanced society to limits that I wouldn’t have imagine possible, which also lead to it HELPING a lot of people overall, as well as made things more accessible for the disabled: prosthetics, eye care, hearing impaired, etc, the list goes on. Typically technology BENEFITS EVERYONE and has a POSITIVE effect (ahem… I know what you’re thinking just go with it haha), but in the case of A.I, it has lead to the false impression of a utopia that simply WILL NEVER EXIST! One where the robots will do all the work for us so we can just sit back and relax and prosper from it. We looked only a the short term of A.I. and not the long term, and because of that, we are PAYING a hefty price for it. It’s being used to REPLACE us, NOT HELP US. Lastly, I’ll also be covering a few HUGE security risks and COPY right laws that come into factor regarding it. This article is a part of the Danger! Series, which is where I raise more Cyber Security awareness about critical flaws and vulnerabilities that exist within various system infrastructures, including any protocols and data communication methods, and the Dangers of what could happen should they be exploited to the fullest extent. I also go over various mitigation strategies that can be used to prevent them as well. If by chance there is an exploit video for me showing the full potential risk, it will be included in the advanced version of this article for PAID patreon members only! Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I am going to show you how to write your own custom reveshell script that can perform RCE on any system. This is taking inspiration from reveddshells which have a series of RCE shells that you can download and interact with that will allow you to seamlessly achieve RCE for any remote file upload exploit. Why am I covering this despite there being a site that allows you to do so? Well, much like all things involving hacking you’ll run into situations where you need to write more complex code, even code that is pre-made beforehand for an exploit which might go out of the scope of what you need said program to do. This is also due to the fact that various detection systems are able to identify signature patterns. If you know how to write your own code you can apply further obfuscation methods that will allow you to bypass security. I am also going to show you how the code works under the hood so that you have a CLEAR understanding of how it works and how to write it yourself. This WILL be in the lab upcoming, so I recommend you get good with this as the REAL exploit for the next lab is going to be a lot more complex. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I’m going to show you how to write your own SSH client via Python that you can use to connect to ANY SSH service and pipe in commands to the server. The main little goal of this exercise is to teach you how the SSH protocol works under the hood. What you do with this information, which like all things, can also be used for hacking. I will also eventually be covering how to write your one SSH server which can come in handy. The issue with this is there have been reports of people having issues with the module working. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

For today’s tool video, I’m going to show you how to use the smbclient tool in order to sniff out and exploit smb file shares on windows systems to retrieve a sensitive file that contains password end user credentials. File shares are one of the most CRITICAL end points to protect on any system. There’s a reason why OS systems CLOSE their ports by default on most systems. Should a threat actor be able to breach the service, they will have access to any and all file shares on the system, as well as being able to upload and replace and or tamper with files within the FTP service. This can lead to a lot more complex exploits like living off the land for example. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

For today’s tool video, I’m going to show you how to use wireshark to sniff out network traffic to spy on sensitive credentials that are sent, and WHY you should NEVER use a site unless it has HTTPS enabled on it. Be mindful, just because a site does have HTTPS enabled doesn’t mean it’s safe and secure. Threat actors tend to have phishing sites that enable the protocol to trick us into thinking it’s legit. The wireshark tool, which is used for network traffic analysis, can also be used for a variety of protocol analysis, even for stuff like VOIP eavesdropping, which can allow you to spy on people’s phone call conversations over corporate networks. I’ll eventually cover stuff like that in future parts involving the tool later on. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I'm going to show you how to program servo motors in arduino. The main goal is to “simulate” and show you how programming them for drones work under the hood. I’ll of course leave the working code attached. Just pay attention to how I write the code and go about the overall process and you’ll be fine. For this demonstration I’ll be covering how to program them via the standard ones that come with the arduino kit. I’ll also show you how to program them via ESC motors for the drone. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today I’m going to show you how to program LCD screens. This is staple if you get crafty and want to program CUSTOM stuff like *cough* visualizers that print your emojis to the screen. I’ll be showing you how to program TWO versions of LCD screens that you’ll commonly see in the arduino kit for beginners. 1 of them is the standard one with MANY pin connectors attached to them which can be the most complex to setup. The other is one that is commonly and easily interchangeable which includes a ISC adapter attached to them which is seamless to install and program. I recommend knowing how to program both of them so you can make either work in case you are running short on supplies, OR, in the event you ONLY have one or the other. None the less it’s still staple to know how to program BOTH of them. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today’s exploit video will feature something that has been HEAVILY requested by many of my followers… BINARY injection, also known commonly as a Buffer Overflow exploit. Much like how SQL injection is hard to learn without proper instruction, so is binary injection. What I’m going to show you today is the overall premise and concept behind the technique. This is the DEFINITIVE example and BEST way to EASILY explain how binary injection works to ANYONE that wants to learn more about it. Binary is overall one of the HARDEST techniques to learn and master mostly due to there being FEW GOOD resources that can teach it to you. I’m also going to write some sample code in C that will be vulnerable to buffer overflow attacks, so that you can play with it and get a feel for how it works on a technical level. This will also set us up for the next part, which will be me covering how to use a debugger to analyze the code flow, as well as perform the overall exploit the manual way. There are more special surprises for binary injection coming up so do stay tuned. As always, any and all videos that are included with this article will be for PAID members only! You can check out my tiers and pricing down in my patreon link in the comment section below as well as on my website. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

Today, I’m going to dive further into binary injection exploits, and cover how to exploit them for RCE, remote code execution. I’m also going to show you how to use one of the most common tools that is used to analyze code flow as well as binary applications overall which is the GDB debugger. I’ll explain a bit about what that is as well. Last time, I showed you how to exploit vulnerable functions inside of a program via end user input in order to call other functions within the program via memory EVEN if the function is NEVER explicitly called in the program itself. This was to highlight the dangers of leaving vulnerable code within an application and how it can be exploited by threat actors to execute it which can be problematic if you’ve left stuff like backdoors in the code that the threat actor can easily piggyback off of to compromise internal infrastructures. This time around, we are going to take it a step further and exploit the overall application to have it perform ANY form of RCE that we want against a target application whether it be in plain text format or binary format. This is a CRUCIAL skill to master, as you’ll often run into various CTF challenges that require you to know binary exploitation, as well as overall in general if you are running some security tests. It overall comes in handy if you’re just a hacker in general and is a STAPLE skill to master. You’ll go a long way, ESPECIALLY if you plan to do forensic with this skill set. Disclaimer As always, personal disclaimer, any and all information for this is strictly for educational purposes and I do not condone any form of illegal activity, nor am I responsible for anything you should use this information for. DO NOT pen-test on anyone's network unless it is your own, or you have permission to do so. Now, let’s begin! - The Hacker Who Laughs 🕸🕸🎃🕸🕸

This is a custom portable CTF server that I wrote in: HTML/CSS/JS, and PHP.
The server is designed to allow you to pentest wherever you are locally vs the traditional means of having to be connected to the internet in order to engage in web application pentesting CTF challenges, allowing you to get practice wherever you are on the go.

Today’s exploit video will feature something that has been HEAVILY requested by many of my followers… BINARY injection, also known commonly as a Buffer Overflow exploit specifically for 64 bit.
Much like how SQL injection is hard to learn without proper instruction, so is binary injection. This will be for beginners.