Futaba _ Webs 🕸🕸🎃🕸🕸
The Art of Code Analysis 🕸🕸🎃🕸🕸
Today's article is going to focus on how to conduct PROPER code analysis. You might even say that by the end of this article, you’ll also have an idea on HOW to properly read and analyze code altogether, which is an important skill set whether it be for Cyber, hacking, or areas like Software Engineering that MANY struggle with, more so since a lot of code typically is poorly documented, if any at all exits, which can be problematic for those that don’t know how to navigate the unknown without it. You shouldn’t have to of course, but in the wild, it’s what you’re going to see so it’s best to get good at it, more so if you're a security analyst and hacker overall. Threat actors aren't going detail how their stuff works. That's NONSENSE and would be silly!
🎃 Article 🎃 Glossary 🎃 Catalog 🎃 Home 🎃 Search Mode🎃 Article Glossary
🕸 Synopsis 🕸
Today's article is going to focus on how to conduct PROPER code analysis. You might even say that by the end of this article, you’ll also have an idea on HOW to properly read and analyze code altogether, which is an important skill set whether it be for Cyber, hacking, or areas like Software Engineering that MANY struggle with, more so since a lot of code typically is poorly documented, if any at all exits, which can be problematic for those that don’t know how to navigate the unknown without it. You shouldn’t have to of course, but in the wild, it’s what you’re going to see so it’s best to get good at it, more so if you're a security analyst and hacker overall. Threat actors aren't going detail how their stuff works. That's NONSENSE and would be silly!
* giggles while recalling my previous article *
It's not like Cyber Security professionals publicly do this on a daily basis right? RIGHT?
I’m going to explain how to analytically and strategically approach the unknown and figure out what makes it tick altogether, with a sample of some of the stuff I’m working on for my next series so you can easily follow along.
I’m also going to explain how to turn offense into defense which is something I’m really good at despite me NOT specializing in blue teaming.
🕸 Article Topics 🕸
I'll be discussing the following topics in order: 🎃 Learn The Language 🎃 Break The System Apart 🎃 Document As You Go 🎃 Exploit The Code You can click on any of the topics to simply check that one out if it interests you! NOTE: Articles are read from LEFT to RIGHT via 2 columns! Read the first column all the way down and then move to the next one!
🕸 Key Links 🕸
Here's a quick run down on all the main links that are in the article in case you want to check them out first. 🎃 LinkedIn Version
🎃 The Art of Code Analysis
Learn The Language 🕸🕸🎃🕸🕸
It’s a no brainer on this one…. But YES, LEARN…THE….LANGUAGE! Remember, you CAN reverse engineer and put two and two together, but you’re better off knowing the native language, otherwise you’ll not only have to research the language itself as you study it, but the code itself, on top of any unique techniques that might be embedded within the code. By simply being somewhat knowledgeable about the language first, from there, you can simply worry about studying the code for any vulnerabilities that might exist within it.
There are resources like W3 schools for example that can increase your level of literacy in a language depending on how experienced you are already with a programming language. For me this is about 12 hours per language to be prepped and ready in case I don't know the language.
Part of the main reason I know many programming languages is to avoid having to learn a new one. I'm literate in many already and can read and pick up as I go, which allows me to FOCUS on the analysis.
Break The System Apart 🕸🕸🎃🕸🕸
One of the many benefits of studying code analysis, whether it be for vulnerability assessments or forensics malware analysis, is you get to “break” the system apart and see what makes it tick. This is where you get your hands dirty and REALLY get under the hood to properly understand how the system works.
Whether you be a threat actor or a professional who does things ethical offensively/defensively, This is a great opportunity to to learn, more so if you’re on the more offensive side of things, as you’ll not only be tasked with finding vulnerabilities and figuring out how to mitigate them, but threat modeling various attack vectors that are possible should a vulnerability exist within the code, meaning…. YOU GET HANDS ON EXPERIENCE CRAFTING EXPLOITS/SCENARIOS depending on which side you’re on which is the fun part. This also, of course, depends on the role you work for and overall responsibilities. This is also where you “learn” more complex programming techniques related to your area of choice in Cyber.
When you’re analyzing code, you want to get into the habit of breaking down each line of code at a time. Each line has a story to tell, and you might miss something if you overlook it no matter how simple it is.
For example, there was a set of JS code I was studying a while back for the new malware analysis series I’m working on. The code revolved around DOS’ing a server, but at a quick glance I assumed the way the code was behaving had much to do with overloading the web application server via HTTP requests only, HOWEVER, what I overlooked was memory overloads that were being used to crash the server. Each time the code ran, it behaved in a manner that would cause the server to store more and more memory which is unethical, which can lead to an eventual crash in the long run, more so since it is used for loops to enhance the process. For those that don’t know, using for loops consumes quite an amount of memory, and without proper memory deallocation techniques, with today’s modern processing power, you can crash a system in seconds.
By properly analyzing the code flow, I was able to both formulate a mitigation to the threat, as well as figuring out crafty ways to abuse the exploit.
Document As You Go 🕸🕸🎃🕸🕸
Many will love this, many will hate this, but DOCUMENT AS YOU GO! Each time you break the system apart, write comments next to each line. Get into the habit of that, as this will also teach you CLEAN programming habits in the overall long run.
It’s also a way for you to logically and algorithmically study the code flow, as well as leave “soft” bread crumbs that explain it to the next person that needs to read over your findings. This is also just, again, SMART practice! If you pull the comments apart, if you’ve been documenting everything properly, you’ll also already have a ton of documentation on the matter already, saving you time on writing the official documentation later on as you can simply extract from that.
How to properly document? Take a look at this quick sample of some of the code I’ve dissected for the first malware analysis I’m working on. THIS is what I mean by “breaking” the system apart, as well as documenting as you go. Each line is documented and thoroughly explained with my overall thought process, as well as being constructed with theories/hypotheses to further interpret the overall science behind the code.
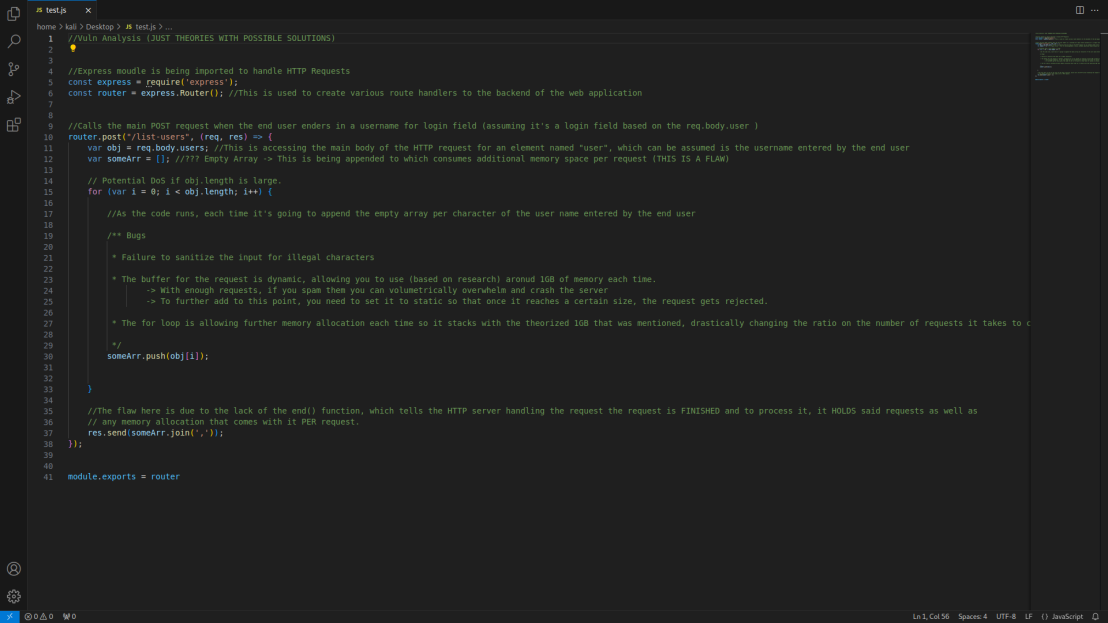
Exploit The Code 🕸🕸🎃🕸🕸
Ever hear the saying “a good defense, makes a good offense”? Well… the same could be said in reverse ESPECIALLY when it comes to Cyber.
Regardless if you’re on defense, figuring out how to exploit something TELLS you HOW to defend something. I don’t specialize in blue teaming, BUT, because I’m exceptional when it comes to offense, I can figure out my defense from that.
I want you to go back to that snippet I made earlier. Remember how the comments focus on weaknesses I’m addressing in the code? You can take what you found and craft exploits with them. You can turn defense into offense, and offense into defense. You’ve just gotta be smart about HOW you go about it.
If you enjoyed this post give it a thumbs up! I’ll be keeping track of whose reacting from now on as there is a “special” reason for it. Just know the more you support my content the more there is in stored!
- The Hacker Who Laughs 🕸🕸🎃🕸🕸







