Futaba _ Webs 🕸🕸🎃🕸🕸
Subnetting For Dummies 🕸🕸🎃🕸🕸
Today’s article is gonna be an interesting one, where I cover one of the most complicated topics CRUCIAL to ETHICAL Cyber Security practices.… SUBNETTING!!!!
🎃 Article 🎃 Glossary 🎃 Catalog 🎃 Home 🎃 Search Mode🎃 Article Glossary
🕸 Synopsis 🕸
Today’s article is gonna be an interesting one, where I cover one of the most complicated topics CRUCIAL to ETHICAL Cyber Security practices.… SUBNETTING!!!! You see… subnetting is NOT hard. It’s rather simple. The PROBLEM, like all things, is that people, REALLY intelligent people, lack the proper soft skills to explain it correctly to you. Over the course of this article I’m going to use non-conventional and more fun ways to properly break down subnetting to you so it “clicks”. It is ESSENTIAL that you UNDERSTAND subnetting as it also comes into play for offensive security when you have to navigate and find all the subnets that exist on a network to see where you can extend your attack surface. I am EXCEPTIONAL at this, as I not only have a full understanding of how subnetting and IP ranges work, BUT, I can “visualize” where I am, as well as make EFFECTIVE usage of basic commands that are commonly overlooked that TELL you how many subnets you have.
🕸 Article Topics 🕸
I'll be discussing the following topics in order: 🎃 What is Subnetting? 🎃 Applying It To Cyber Security? You can click on any of the topics to simply check that one out if it interests you! NOTE: Articles are read from LEFT to RIGHT via 2 columns! Read the first column all the way down and then move to the next one!
🕸 Key Links 🕸
Here's a quick run down on all the main links that are in the article in case you want to check them out first. 🎃 LinkedIn Version
🎃 Subnetting For Dummies
What is Subnetting? 🕸🕸🎃🕸🕸
Subnetting is the art of “splitting” a network into “subnetworks”, which is a network of networks.
Here’s a diagram in order to better visualize it.
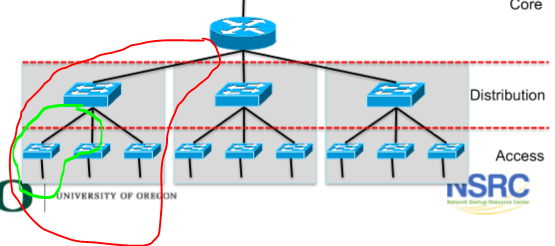
The top of the tree is the “core” network, the main AP that serves as the “exit node” or default gateway which is where all network traffic is routed to and from the network.
The sub trees that you see below are the “subnets”. Ignore the ones below the subnets for now as that’s a bit complicated like explaining recursion. The goal is to keep it simple so you can follow along!
Subnets have what is known as a “subnet mask”, the “/24” that you see commonly attached to a subnet IP address.
Ex: “192.168.1.1/24”
By default, this is the standard subnet mask that is usually assigned to you on a network.
If you apply subnetting you might see stuff like
🎃 “192.168.1.1/23”
🎃 “192.168.1.1/22”
🎃 “192.168.1.1/21”
And so forth. HOWEVER, be mindful THEY ARE NOT THE SAME SUBNET! The “subnet mask” is there to tell you which subnet a system belongs to on a network. Of course, many have differentiating IP addresses to tell the apart for simplicity's sake. It can vary.
You also have stuff like “IP Addresses Classes”, Class A, Class B, Class C, etc.
“OH MY GOD THAT’S SOOOO COMPLICATED” Nahh, not really haha. Classes define the “range pool” of IP addresses that you have available to dish out to systems on the network.
For example, IP Ranges that might look like
“192.168.1.0-255” indicate there is an available pool of 255 IP addresses, the final number being reserved for what is known as the “broadcast address” that is used to echo messages to all systems on the network should you choose to do so, and of course, the first one, which is reserved for the default gateway. You can of course configure these however you like, but it’s kept default for simplicity's sake.
How Does Subnetting Apply To Cyber Security? 🕸🕸🎃🕸🕸
The goal of subnetting is to obfuscate your defenses and avoid what is known as a “monolithic structure”, borrowed from the concept of containers which condense all dependencies for software into one “container”. For Software engineering, this is good practice. HOWEVER, for Cyber Security, this is BAD practice.
When you condense EVERYTHING into one place, you not only create, become a single point of failure, where should an attacker, such as myself, breach your internal network, EVERYTHING is compromised. Imagine I attack one system, and EVERYTHING goes down with it.
Wiggles My Finger at you Like Sonic The HedgeHog
THAT’S NO GOOD!!!!!

- The Hacker Who Laughs 🕸🕸🎃🕸🕸







