Futaba _ Webs 🕸🕸🎃🕸🕸
Man In The Browser Exploit 🕸🕸🎃🕸🕸
Today we are going to talk about Social Engineering, specifically, a "man in the browser" exploit, as well as what social engineering is and how threat actors use it to exploit and leverage a system to gain access. There are various forms of social engineering, and we'll cover them all here today.
🎃 Article 🎃 Glossary 🎃 Catalog 🎃 Home 🎃 Search Mode🎃 Article Glossary
🕸 Synopsis 🕸
Today we are going to talk about Social Engineering, specifically, a "man in the browser" exploit, as well as what social engineering is and how threat actors use it to exploit and leverage a system to gain access. There are various forms of social engineering, and we'll cover them all here today.
🕸 Article Topics 🕸
I'll be discussing the following topics in order: 🎃 Premise 🎃 What is a Man in The Browse Exploit? 🎃 What is a Chromium Driver? 🎃 What is a Physical Hack? 🎃 What is the connection between a Physical hack and Social Engineering? You can click on any of the topics to simply check that one out if it interests you! NOTE: Articles are read from LEFT to RIGHT via 2 columns! Read the first column all the way down and then move to the next one!
🕸 Key Links 🕸
Here's a quick run down on all the main links that are in the article in case you want to check them out first. 🎃 LinkedIn Version 🎃 Patreon Version 🎃 Man In The Browser LIVE Demo 🎃 Chromium Driver
🎃 Man In The Browser Exploit
Premise 🕸🕸🎃🕸🕸
Social engineering is one of the most commonly used tactics, as well as something that is known as a physical hack.
As always, before we dive right into this, some terminology needs to be explained so that you can follow along with the article.
What is a Man in The Browse Exploit? 🕸🕸🎃🕸🕸
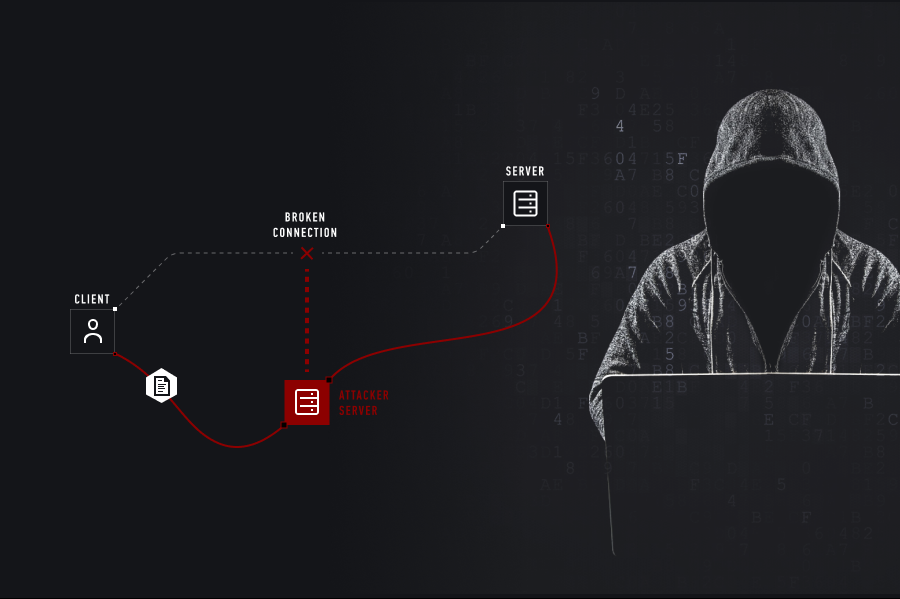
MITB, man in the browser, is a form of social engineering exploit that masquerades as your favorite web browser in order to phish sensitive credentials out of you, and is considered a form of a man in the middle attack. It's such an exact copy that you literally cannot tell the difference. The only difference you'll notice is that your "sessions" don't seem to quite be there. What do I mean by that? Ever opened a browser in private mode and realized you had to log back into all of your stuff? That's what I'm talking about, except it doesn't have the little incognito icon or any indicators you are used to seeing that would give it away, or at least NOT anymore. If the attacker is smart, then they can locate where cookies and saved data are stored onto the system, and then integrate it into this, BUT, that would defeat the purpose of having you re-enter them in again manually so they can exploit you.
Even still this form of exploit will trick you just the same. It even has the exact settings and pages, and features as the original, because it IS the original, technically. This allows you to steal credentials and other forms of sensitive information such as cookies for example from end user browser sessions.
The most dangerous part about this exploit is that:
🎃 One, it's custom and can go beyond the typical scope of just phishing data from unsuspecting end users, and
🎃 Two, it takes advantage of the fact you ALWAYS, have your browser open and that you are constantly clicking away at those little keystrokes of yours. This means you can get two for one and install all sorts of malware, run background processes, and even install a keylogger on the system and send data to a remote server you have to log end user credentials. It can get even more scary if you can replicate a screen watch feature in the meterpreter shell to watch the end users screen as they type. This allows you to bypass stuff like MFA, where you can see the EXACT token information being sent.
For this project you are going to need something that is known as a "chromium" driver, since we are going to be working with Google Chrome for this exploit. This driver, along with the selenium module has come A LONG WAY. It originally ONLY displayed the chromium browser which was a dead give away, but now, it displays the REAL thing, so there is nothing that gives it away if you manage to spoof the chrome signature and place it on the end user system.
Link to Chromium Driver
What is a Chromium Driver? 🕸🕸🎃🕸🕸
The Chromium driver is what we are going to be using to mimic the chrome browser that is installed on your system, along with a module in python that is called "selenium", which allows you to call up a series of web drivers: chrome, Firefox, etc etc, and launch the real thing, even with a default page. It’s most commonly used for web application development across all resolutions for all browsers.
This is combined with Selenium which is a module in python that allows you to develop test case scenarios for browser integration, for stuff like add on's and extensions, or, if you are the devs, it allows you to test for new in house main features before they are added to the browser.
In the right hand’s, it’s harmless, BUT, in the right hands it can do a lot of damage.
What is a Physical Hack? 🕸🕸🎃🕸🕸
A physical hack is a scenario where the attacker has physical access to the system, and can perform stuff like: inserting a keylogger dongle into systems to log end user keystrokes, installing back-doors and malware, taking advantage of admin access and other trusted systems and services on the network to “live off the land”, as well as bypass security further by disabling firewall systems that might block backdoor access so the attacker can maintain access, which can allow them to further do stuff like: excavate data off the network, further extend their level of access to various other sub-networks and sub domains that might belong to the infrastructure, all while being able to go undetected.
What is the connection between a Physical hack and Social Engineering? 🕸🕸🎃🕸🕸
Social engineering allows you to manipulate people and gain access to the system physically, followed up by a physical hack that allows you to physically gain and maintain access This sets you up to potentially have backdoor access that allows you to tap back into the system undetected and exploit the system as you see fit. This allows you to bypass stuff that you normally wouldn’t be able to if it were only from a digital landscape. Some things can only be done physically due to the level of complexities that might be in place for a system infrastructure.
This is a common tactic that is used , whether it be as a pen-tester that is testing the security in an infrastructure, or as a threat actor that is trying to leverage the system for their own personal gain. They go hand in hand.

If you like to see the more advanced version of this article that talks about methods that can be used to mitigate, as well as any videos included, SUBSCRIBE TO MY PATREON CYBER SECURITY TIER!
If you enjoyed this post give it a thumbs up! I’ll be keeping track of whose reacting from now on as there is a “special” reason for it. Just know the more you support my content the more there is in stored!
- The Hacker Who Laughs 🕸🕸🎃🕸🕸