CTF Server
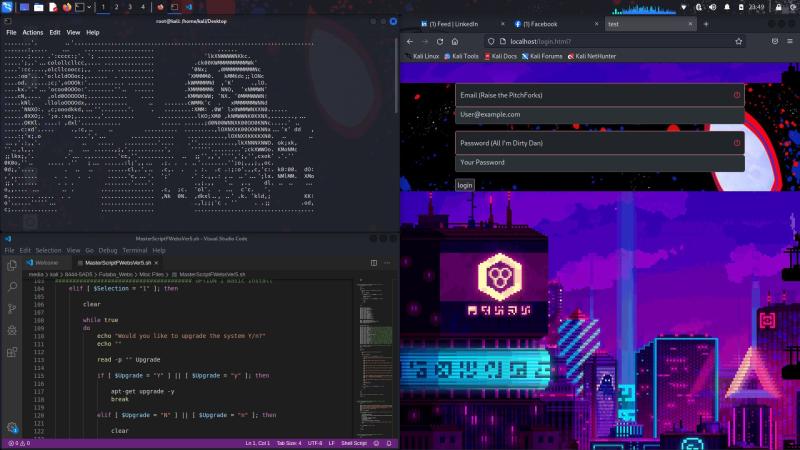
This is a custom portable CTF server that I made! Try it out!
RoyMBull Github
Take a loot at some of my projects available on my GitHub page!
Exploit Videos

Check out some of my live hacking exploit demonstrations.
Python Tools

Check out some of the demo code for my Pent-Testing Tools!
YouPic Feature

I was featured on a photography platform called “YouPic”.



